Today i got an email with the subject Invoice 622476180 05/17/2017 that had the following PDF attached:
Checksums for Invoice 622476180 05_17_2017.PDF:
MD5 (Invoice 622476180 05_17_2017.PDF): 14d05276125e70d43e710ef186261c95
SHA1 (Invoice 622476180 05_17_2017.PDF): 7d6606542484d7b50ccfdb1d4fa310f679bf6ba4
SHA256 (Invoice 622476180 05_17_2017.PDF): e60a621321fc670f0cac092a01281dd599a6f2fc20651ebc530c0a9912e666c6
Blake2s (Invoice 622476180 05_17_2017.PDF): 0fca6361af4c77031f79446a86bb1ed1646b85d80cae1f368d9a41fd2cd5d892
Blake2b2 (Invoice 622476180 05_17_2017.PDF): 6316fd526699ce342bd8a2ebae14d3275693e79ed244a787360d2089aa7c9885
VirusTotal told me it is malicious and known:
14d05276125e70d43e710ef186261c95 [11/55] IS KNOWN by VirusTotal
Engine 'McAfee-GW-Edition' (Version v2015) detects as 'Artemis', since update 20170516
Engine 'ZoneAlarm' (Version 1.0) detects as 'HEUR:Trojan-Downloader.Script.Generic', since update 20170517
Engine 'NANO-Antivirus' (Version 1.0.76.16894) detects as 'Trojan.Ole2.Vbs-heuristic.druvzi', since update 20170517
Engine 'Qihoo-360' (Version 1.0.0.1120) detects as 'virus.office.obfuscated.1', since update 20170517
Engine 'Symantec' (Version 1.3.1.0) detects as 'Trojan.Pidief', since update 20170517
Engine 'Fortinet' (Version 5.4.233.0) detects as 'WM/TrojanDownloader.7A51!tr', since update 20170517
Engine 'CAT-QuickHeal' (Version 14.00) detects as 'O97M.Downloader.AJK', since update 20170517
Engine 'McAfee' (Version 6.0.6.653) detects as 'Artemis!14D05276125E', since update 20170517
Engine 'Panda' (Version 4.6.4.2) detects as 'O97M/Downloader', since update 20170516
Engine 'Rising' (Version 28.0.0.1) detects as 'Heur.Macro.Downloader.d (classic) ', since update 20170517
Engine 'Ikarus' (Version 0.1.5.2) detects as 'Trojan-Downloader.VBA.Agent', since update 20170517
PDFid indicated that it is indeed suspicious:
PDFiD 0.2.1 Invoice 622476180 05_17_2017.PDF
PDF Header: %PDF-1.4
obj 15
endobj 15
stream 4
endstream 4
xref 1
trailer 1
startxref 1
/Page 1
/Encrypt 0
/ObjStm 0
/JS 2 << Javascript
/JavaScript 3 << Javascript
/AA 0
/OpenAction 1 << action on opening the PDF
/AcroForm 0
/JBIG2Decode 0
/RichMedia 0
/Launch 0
/EmbeddedFile 1 << file embedded
/XFA 0
/Colors > 2^24 0
Actually the PDF contains 2 scripts (script_-1468562363504637198.js, script_-2641379014723298464.js) and an Office document (docm) file.
Checksums for attached_ZLOYY.docm:
MD5 (attached_ZLOYY.docm): 6cdc2649cba1a042f2db4e49ffcdfb6b
SHA1 (attached_ZLOYY.docm): f6b74cf99e7f43bec841cb72f393b787df2e811d
SHA256 (attached_ZLOYY.docm): 635d562c684e49247af1939380a662e3630c0bc675cf71bcbb13577a3f772fde
Blake2s (attached_ZLOYY.docm): 8c7079c3d0c50369f0a0a9bf10a18db90feb454008e29e378b371f79a54df5e0
Blake2b2 (attached_ZLOYY.docm): 502131858d04bf07a21a73250df900f6adfa6d1d52437b72e70c49fe50361c70
6cdc2649cba1a042f2db4e49ffcdfb6b [8/58] IS KNOWN by VirusTotal
Engine 'NANO-Antivirus' (Version 1.0.76.16894) detects as 'Trojan.Ole2.Vbs-heuristic.druvzi', since update 20170517
Engine 'Qihoo-360' (Version 1.0.0.1120) detects as 'virus.office.obfuscated.1', since update 20170517
Engine 'TrendMicro' (Version 9.740.0.1012) detects as 'HEUR_VBA.O2', since update 20170517
Engine 'ZoneAlarm' (Version 1.0) detects as 'HEUR:Trojan-Downloader.Script.Generic', since update 20170517
Engine 'Ikarus' (Version 0.1.5.2) detects as 'Trojan-Downloader.VBA.Agent', since update 20170517
Engine 'Panda' (Version 4.6.4.2) detects as 'O97M/Downloader', since update 20170516
Engine 'Fortinet' (Version 5.4.233.0) detects as 'WM/TrojanDownloader.7A51!tr', since update 20170517
Engine 'CAT-QuickHeal' (Version 14.00) detects as 'O97M.Downloader.AJK', since update 20170517
Basically when the PDF is opened by a viewer it will launch the embedded docm file.
The docm file again contains scripts that will be executed when launched.
The scripts within the docm file trigger the download of the actual malicious payload from the following URL http://evasalome.nl/hjt67t.
What is downloaded from the before mentioned URL is not directly executable, it is somehow obfuscated. Lets have a look at the file:
00000000 1c 1d d9 70 7a 6b 4f 47 57 5a 37 4f ae 8f 68 5a |...pzkOGWZ7O..hZ|
00000010 fc 4e 73 6e 41 68 47 30 16 41 4d 71 6c 4f 47 68 |.NsnAhG0.AMqlOGh|
00000020 51 47 49 70 79 6b 4f 47 53 5a 37 4f 51 70 68 5a |QGIpykOGSZ7OQphZ|
00000030 44 4e 73 6e 41 68 47 30 56 41 4d 71 ec 4f 47 68 |DNsnAhG0VAMq.OGh|
00000040 5f 58 f3 7e 79 df 46 8a 72 e2 36 03 9c 51 3c 32 |_X.~y.F.r.6..Q<2|
00000050 2d 3d 53 1e 33 07 20 42 37 2c 6d 12 0d 21 29 07 |-=S.3. B7,m..!).|
00000060 25 67 2b 15 59 19 3a 29 73 33 59 6f 15 3f 3b 7a |%g+.Y.:)s3Yo.?;z|
00000070 29 21 17 0b 6f 65 4a 3a 72 41 4d 71 6c 4f 47 68 |)!..oeJ:rAMqlOGh|
00000080 01 02 49 70 35 6a 4b 47 bb e8 2e 16 51 70 68 5a |..Ip5jKG....QphZ|
00000090 44 4e 73 6e a1 68 48 31 5d 40 4b 71 6c ef 46 68 |DNsn.hH1]@Kql.Fh|
000000a0 51 97 48 70 79 6b 4f 47 4f fc 36 4f 51 60 68 5a |Q.HpykOGO.6OQ`hZ|
000000b0 44 fe 72 6e 41 68 07 30 56 51 4d 71 6c 5f 47 68 |D.rnAh.0VQMql_Gh|
000000c0 55 47 49 70 79 6b 4f 47 57 5a 37 4f 51 70 68 5a |UGIpykOGWZ7OQphZ|
000000d0 44 ce 70 6e 41 78 47 30 d7 bc 4f 71 6e 4f 47 68 |D.pnAxG0..OqnOGh|
000000e0 51 47 59 70 79 7b 4f 47 53 5a 27 4f 51 60 68 5a |QGYpy{OGSZ'OQ`hZ|
000000f0 44 4e 73 6e 51 68 47 30 56 41 4d 71 6c 4f 47 68 |DNsnQhG0VAMqlOGh|
00000100 2d fd 48 70 7d 6a 4f 47 53 3a 34 4f 51 6d 68 5a |-.Hp}jOGS:4OQmhZ|
00000110 44 4e 73 6e 41 68 47 30 56 41 4d 71 6c 4f 47 68 |DNsnAhG0VAMqlOGh|
00000120 51 47 49 70 79 6b 4f 47 53 5a 37 4f 51 70 68 5a |QGIpykOGSZ7OQphZ|
00000130 44 4e 73 6e 41 68 47 30 56 41 4d 71 6c 4f 47 68 |DNsnAhG0VAMqlOGh|
00000140 51 47 49 70 79 6b 4f 47 53 5a 37 4f 51 70 68 5a |QGIpykOGSZ7OQphZ|
00000150 44 4e 73 6e 41 68 47 30 56 f1 4c 71 24 4c 47 68 |DNsnAhG0V.Lq$LGh|
00000160 51 47 49 70 79 6b 4f 47 53 5a 37 4f 51 70 68 5a |QGIpykOGSZ7OQphZ|
00000170 44 4e 73 6e 41 68 47 30 78 35 28 09 18 4f 47 68 |DNsnAhG0x5(..OGh|
00000180 df df 48 70 79 7b 4f 47 53 fa 36 4f 51 60 68 5a |..Hpy{OGS.6OQ`hZ|
00000190 44 4e 73 6e 41 68 47 30 56 41 4d 71 4c 4f 47 08 |DNsnAhG0VAMqLOG.|
000001a0 7f 35 2d 11 0d 0a 4f 47 13 47 37 4f 51 c0 69 5a |.5-...OG.G7OQ.iZ|
000001b0 44 6e 73 6e 41 d8 46 30 56 41 4d 71 6c 4f 47 68 |DnsnA.F0VAMqlOGh|
000001c0 51 47 49 70 39 6b 4f 07 7d 3e 56 3b 30 70 68 5a |QGIp9kO.}>V;0phZ|
000001d0 18 c9 72 6e 41 b8 46 30 56 d1 4d 71 6c 9f 46 68 |..rnA.F0V.Mql.Fh|
000001e0 51 47 49 70 79 6b 4f 47 53 5a 37 4f 11 70 68 9a |QGIpykOGSZ7O.ph.|
000001f0 6a 3c 00 1c 22 68 47 30 56 5c 4d 71 6c 2f 44 68 |j<.."hG0V\Mql/Dh|
00000200 51 67 49 70 79 0b 4d 47 53 5a 37 4f 51 70 68 5a |QgIpy.MGSZ7OQphZ|
00000210 44 4e 73 6e 01 68 47 70 56 41 4d 71 6c 4f 47 68 |DNsn.hGpVAMqlOGh|
00000220 51 47 49 70 79 6b 4f 47 53 5a 37 4f 51 70 68 5a |QGIpykOGSZ7OQphZ|
00000230 44 4e 73 6e 41 68 47 30 56 41 4d 71 6c 4f 47 68 |DNsnAhG0VAMqlOGh|
00000240 51 47 49 70 79 6b 4f 47 53 5a 37 4f 51 70 68 5a |QGIpykOGSZ7OQphZ|
00000250 44 4e 73 6e 41 68 47 30 56 41 4d 71 6c 4f 47 68 |DNsnAhG0VAMqlOGh|
00000260 51 47 49 70 79 6b 4f 47 53 5a 37 4f 51 70 68 5a |QGIpykOGSZ7OQphZ|
00000270 44 4e 73 6e 41 68 47 30 56 41 4d 71 6c 4f 47 68 |DNsnAhG0VAMqlOGh|
00000280 51 47 49 70 79 6b 4f 47 53 5a 37 4f 51 70 68 5a |QGIpykOGSZ7OQphZ|
00000290 44 4e 73 6e 41 68 47 30 56 41 4d 71 6c 4f 47 68 |DNsnAhG0VAMqlOGh|
000002a0 51 47 49 70 79 6b 4f 47 53 5a 37 4f 51 70 68 5a |QGIpykOGSZ7OQphZ|
[...]
Note the pattern QGIpykOGSZ7OQphZDNsnAhG0VAMqlOGh that is reoccuring from offset 0x200 onward.
An educated guess is that the file is obfuscated with XOR and at this place (offset 0x200 - 0x2a0) the obfuscated file contains null bytes, and therefore exposes the key used for the rolling xor obfuscation used.
Let’s verify this educated guess.
We take the downloaded file (md5: 716165fb5e07ecc95d45e8761b10ab30) and xor it with QGIpykOGSZ7OQphZDNsnAhG0VAMqlOGh.
You can use my golang rolling xor implementation from gist like this.
After you built the above code you can use it as follows to undo the xor encryption.
xor -s QGIpykOGSZ7OQphZDNsnAhG0VAMqlOGh -f hjt67t -o hardiloch8.exe
Et voila, we get a MZ Header:
00000000 4d 5a 90 00 03 00 00 00 04 00 00 00 ff ff 00 00 |MZ..............|
00000010 b8 00 00 00 00 00 00 00 40 00 00 00 00 00 00 00 |........@.......|
00000020 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
00000030 00 00 00 00 00 00 00 00 00 00 00 00 80 00 00 00 |................|
00000040 0e 1f ba 0e 00 b4 09 cd 21 b8 01 4c cd 21 54 68 |........!..L.!Th|
00000050 69 73 20 70 72 6f 67 72 61 6d 20 63 61 6e 6e 6f |is program canno|
00000060 74 20 62 65 20 72 75 6e 20 69 6e 20 44 4f 53 20 |t be run in DOS |
00000070 6d 6f 64 65 2e 0d 0d 0a 24 00 00 00 00 00 00 00 |mode....$.......|
00000080 50 45 00 00 4c 01 04 00 e8 b2 19 59 00 00 00 00 |PE..L......Y....|
00000090 00 00 00 00 e0 00 0f 01 0b 01 06 00 00 a0 01 00 |................|
000000a0 00 d0 01 00 00 00 00 00 1c a6 01 00 00 10 00 00 |................|
000000b0 00 b0 01 00 00 00 40 00 00 10 00 00 00 10 00 00 |......@.........|
000000c0 04 00 00 00 00 00 00 00 04 00 00 00 00 00 00 00 |................|
000000d0 00 80 03 00 00 10 00 00 81 fd 02 00 02 00 00 00 |................|
000000e0 00 00 10 00 00 10 00 00 00 00 10 00 00 10 00 00 |................|
000000f0 00 00 00 00 10 00 00 00 00 00 00 00 00 00 00 00 |................|
00000100 7c ba 01 00 04 01 00 00 00 60 03 00 00 1d 00 00 ||........`......|
00000110 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
00000120 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
00000130 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
00000140 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
00000150 00 00 00 00 00 00 00 00 00 b0 01 00 48 03 00 00 |............H...|
00000160 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
00000170 00 00 00 00 00 00 00 00 2e 74 65 78 74 00 00 00 |.........text...|
00000180 8e 98 01 00 00 10 00 00 00 a0 01 00 00 10 00 00 |................|
00000190 00 00 00 00 00 00 00 00 00 00 00 00 20 00 00 60 |............ ..`|
000001a0 2e 72 64 61 74 61 00 00 40 1d 00 00 00 b0 01 00 |.rdata..@.......|
000001b0 00 20 00 00 00 b0 01 00 00 00 00 00 00 00 00 00 |. ..............|
000001c0 00 00 00 00 40 00 00 40 2e 64 61 74 61 00 00 00 |....@..@.data...|
000001d0 5c 87 01 00 00 d0 01 00 00 90 00 00 00 d0 01 00 |\...............|
000001e0 00 00 00 00 00 00 00 00 00 00 00 00 40 00 00 c0 |............@...|
000001f0 2e 72 73 72 63 00 00 00 00 1d 00 00 00 60 03 00 |.rsrc........`..|
00000200 00 20 00 00 00 60 02 00 00 00 00 00 00 00 00 00 |. ...`..........|
00000210 00 00 00 00 40 00 00 40 00 00 00 00 00 00 00 00 |....@..@........|
00000220 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
00000230 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
00000240 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
00000250 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
00000260 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
00000270 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
00000280 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
00000290 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
000002a0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
[...]
The file executable has the following checksums and VT coverage:
Checksums for hardiloch8.exe:
MD5 (hardiloch8.exe): f3d9b2cb51e81d12ff3d5faaca231041
SHA1 (hardiloch8.exe): ca7cf9e472f34973216781c3a1e269c510af0300
SHA256 (hardiloch8.exe): 5f1fcdfb951dc4642ce136a5d3e6bc42021f8e0cd631975a5eb3842da020531c
Blake2s (hardiloch8.exe): 30f42a70db4750d571ff448fb575fb158add146441dbf89ba775e7404f726671
Blake2b2 (hardiloch8.exe): 9b38fd14ee22b12e5b97a4b1acc539a4309a0bd5adb462cc0562b637507c123f
hardiloch8.exe: PE32 executable (GUI) Intel 80386, for MS Windows
f3d9b2cb51e81d12ff3d5faaca231041 [11/60] IS KNOWN by VirusTotal
Engine 'SentinelOne' (Version 1.0.0.12) detects as 'static engine - malicious', since update 20170516
Engine 'Paloalto' (Version 1.0) detects as 'generic.ml', since update 20170517
Engine 'Symantec' (Version 1.3.1.0) detects as 'Trojan.Gen.8!cloud', since update 20170517
Engine 'Endgame' (Version 0.5.0) detects as 'malicious (high confidence)', since update 20170515
Engine 'ZoneAlarm' (Version 1.0) detects as 'UDS:DangerousObject.Multi.Generic', since update 20170517
Engine 'Bkav' (Version 1.3.0.8876) detects as 'W32.eHeur.Malware08', since update 20170517
Engine 'Kaspersky' (Version 15.0.1.13) detects as 'UDS:DangerousObject.Multi.Generic', since update 20170517
Engine 'Webroot' (Version 1.0.0.207) detects as 'W32.Ransomware.Jaff', since update 20170517
Engine 'CrowdStrike' (Version 1.0) detects as 'malicious_confidence_63% (W)', since update 20170130
Engine 'VBA32' (Version 3.12.26.4) detects as 'SScope.TrojanRansom.WannaCry', since update 20170517
Engine 'Invincea' (Version 6.3.0.25213) detects as 'worm.win32.gamarue.au', since update 20170516
But what is it. What does the file do. Well we can try it out and execute it in a safe environment.
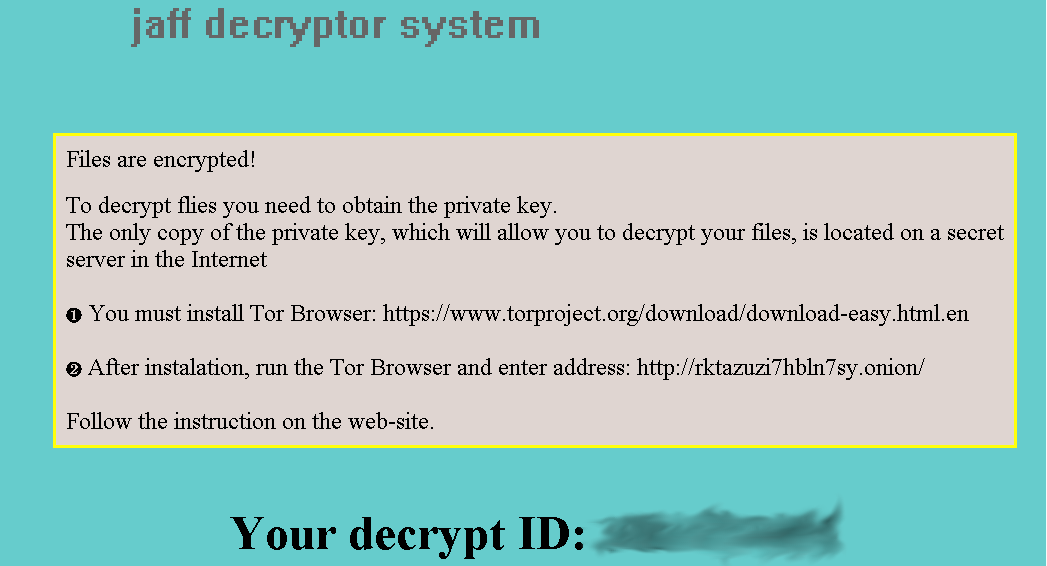
The Ransomware guys hide behind http://rktazuzi7hbln7sy.onion/
Wehn you enter an ID, you get a bitcoin addr to pay the ransom to and some instructions.
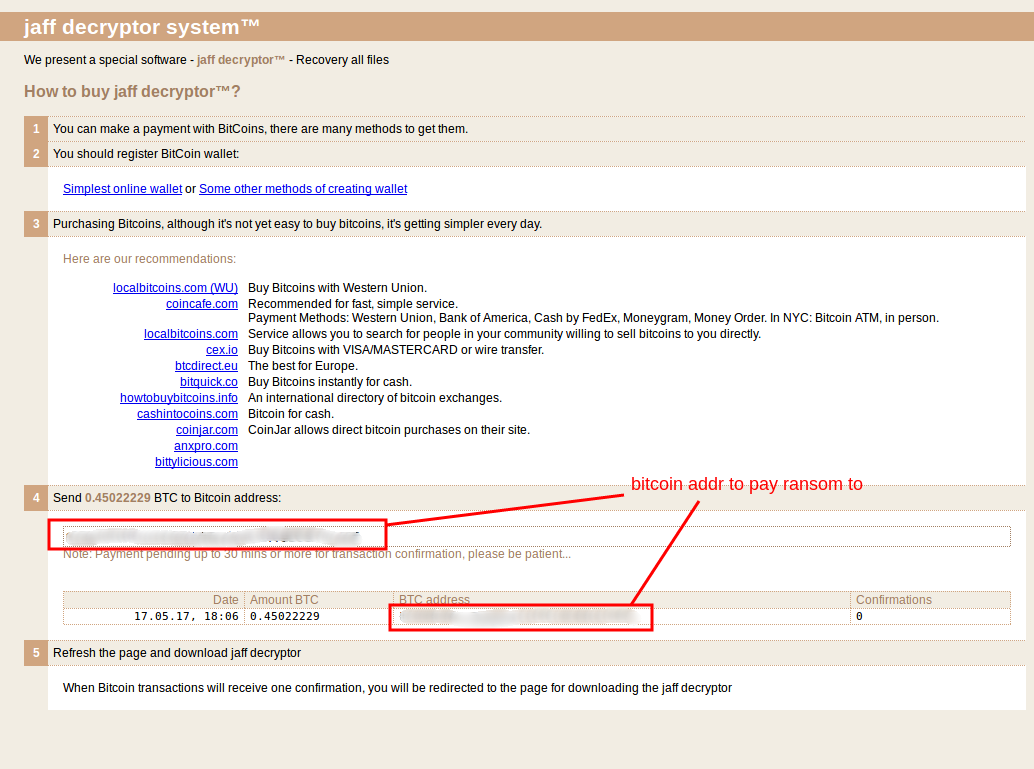
The ransom is quite high, it is currently 814.34 USD
Investigate the sample with IDA
You can find the following PDB String in the binary. This is the Path where the developer of the malware used to store it’s code for this malware.
D:\\Arena\\Cryptor_AES-RSA_V13\\Release\\Encoder.pdb
More digging into it will be done in the next post (or not, depends on my time).